Endpoint Detection & Response (EDR) , Endpoint Security , Governance & Risk Management
Connected Devices Could Allow Attackers to Target Industrial Systems, Trend Micro Reports
The increasing use of internet-connected devices within manufacturing facilities is opening up new ways for hackers to target so-called "smart" factories with unconventional attack methods, according to an analysis by security firm Trend Micro and the Polytechnic University of Milan.
See Also: 451 Research Report: Tackling the Visibility Gap in Information Security
Using Polytechnic University's Industry 4.0 Lab, Trend Micro researchers demonstrated how malicious actors can hack into industrial internet of things, or IIoT, environments by gaining a foothold in one network and then moving laterally through the interconnected infrastructure, according to a report published this week.
To conduct their experiment, the researchers created a connected factory using the same fundamental principles found on full-fledged production floors, according to the report. The factory was designed to make toy cell phones.
Smart manufacturing systems are designed to be isolated from company's IT networks as well as the internet, the report notes. With the increasing connectivity between IT and operational technology systems, however, attackers now have access to a larger attack surface and many more endpoints.
The researchers found that attackers could target smart manufacturing systems by using malicious software extensions or Trojanized IIoT devices as well as exploits in mobile human-machine interfaces. These could then be used to leap from IT systems to more isolated OT networks, they say.
Such attacks potentially could lead to intellectual property theft, industrial espionage and possibly sabotage, the report notes.
"As our research shows, there are multiple vectors now exposed to such threats, which could result in major financial and reputational damage for Industry 4.0 businesses," Bill Malik, vice president of infrastructure strategies at Trend Micro, writes in the report.
Entry Points
The report focuses on three ways that an attacker could gain a foothold within a connected manufacturing facility or smart factory:
- Engineering workstations: These workstations, connected to the production floor, are used for developing and deploying program logic, which could be exploited by attackers by compromising the software supply chain.
- Custom IIoT device development environments: Some smart manufacturing systems use custom IIoT devices that are programmed by in-house developers. In many cases, the developers use third-party software libraries to create these devices. Attackers could attempt to add Trojanized components to these software libraries, giving them indirect access to the larger factory network.
- Manufacturing execution system databases: Because these databases store work orders, templates and other manufacturing data, they are trusted by the rest of the factory's network. An attacker with access to the network could alter production by changing the records in the database.
Vulnerabilities and Attacks
The Trend Micro researchers developed several methods to simulate how an attacker might attempt to gain access to a connected facility.
In one scenario, researchers found attackers could gain entry into a smart manufacturing system through malicious industrial add-ins.
Many companies allow workers to download add-ins from industrial app stores to expand the functionality of the hardware they are using. These extensions or apps can become weak spots that attackers can exploit, the report notes.
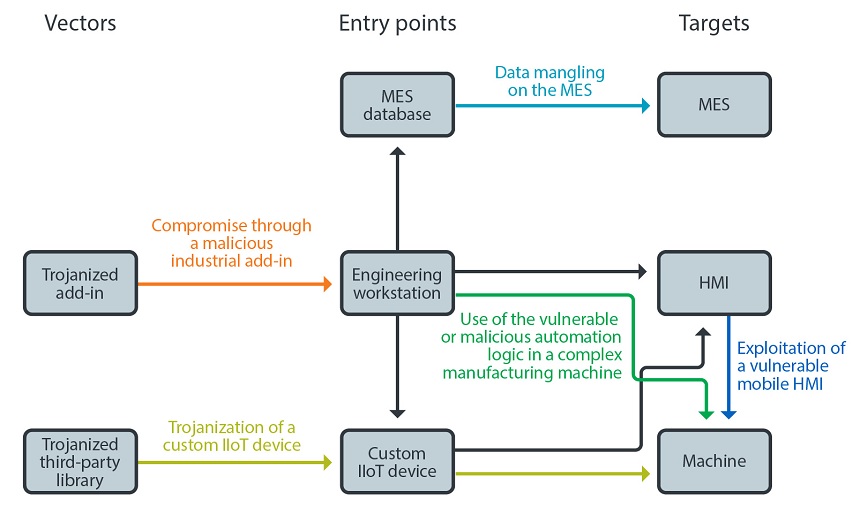
An attacker who has compromised an app used in an engineering workstation could then gain access to the network that controls the factory floor, the researchers say. This could lead to the theft of sensitive data or even the alteration of the factory's production, according to Trend Micro.
Attackers can also cause malfunctions on the factory floor by Trojanizing software used to create custom IIoT devices, the report says.
"Developing custom IIoT devices often involves using resources, tutorials and libraries that are uploaded to publicly accessible repositories that lack a mechanism or vetting process aimed at checking for their integrity," the report notes.
By Trojanizing software, researchers were able to alter temperature readings within the facility, which could cause the factory to shut down due for safety reasons. Also, a threat actor could exploit a vulnerability in a third-party software library used to build a connected devices to cause a denial-of-service attack in a facility, the report notes.
Mobile human-machine interfaces, which are connected to networks through either Wi-Fi or Bluetooth, are also more vulnerable compared to interfaces using conventional wired connections, the report notes. "A malicious app could prompt actions within a mobile human-machine interface, which could then give the attacker control over a factory system."
Advanced Attacks
The Trend Micro analysis notes that many of the scenarios it describes would have to be executed by experienced attackers with the resources and knowledge to exploit these vulnerabilities.
"We believe that unconventional attack vectors such as the ones we explore are more likely for an advanced attacker profile," the report notes. "This possibility is increased by the fact that smart-manufacturing systems, while made of hardware, live in an ecosystem with an intricate net of interdependencies."
"Factory" - Google News
May 14, 2020 at 10:21PM
https://ift.tt/3fNtFZf
'Smart' Factories Could Face Unique Attacks: Report - BankInfoSecurity.com
"Factory" - Google News
https://ift.tt/2TEEPHn
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "'Smart' Factories Could Face Unique Attacks: Report - BankInfoSecurity.com"
Post a Comment